Several of our small business, nonprofit, and education customers run Ubiquiti networks and so I thought it would be helpful to answer the following question using the Unifi Dream Machine Pro.
“How do I prevent users from changing their DNS to bypass filtering?”
While preventing content filter bypass is a good reason to manage DNS ports on your firewall, another often overlooked reason is to impede malware that has entered your network from using other outside DNS resolvers. Forcing all DNS through a DNS firewall or RPZ will insure that all related traffic is properly vetted.
This setup is for configuring DNS firewall rules on a Unifi Dream Machine Pro, but the basic rules and configuration are similar on the USG and USG Pro respectively. This is done in 4 easy steps.
- Create DNS Port Group
- Create Resolver IP Group
- Create rule allowing Resolver IP Group
- Create rule denying DNS Port Group
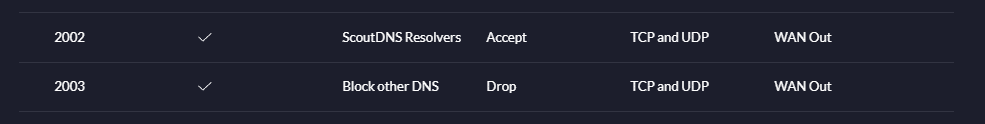
The end result will be something like this:
STEP 1) Configure DNS Port Group
First configure the group objects within the firewall subtab. Object based configuration makes managing systems so much easier. We will start out by configuring a port based object that represents all DNS traffic. Enter Port 53 and call it All DNS.
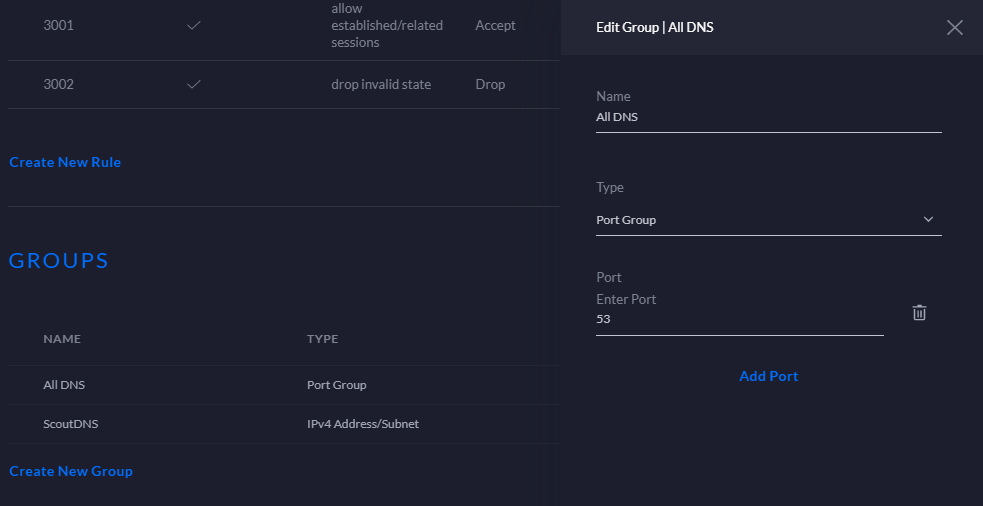
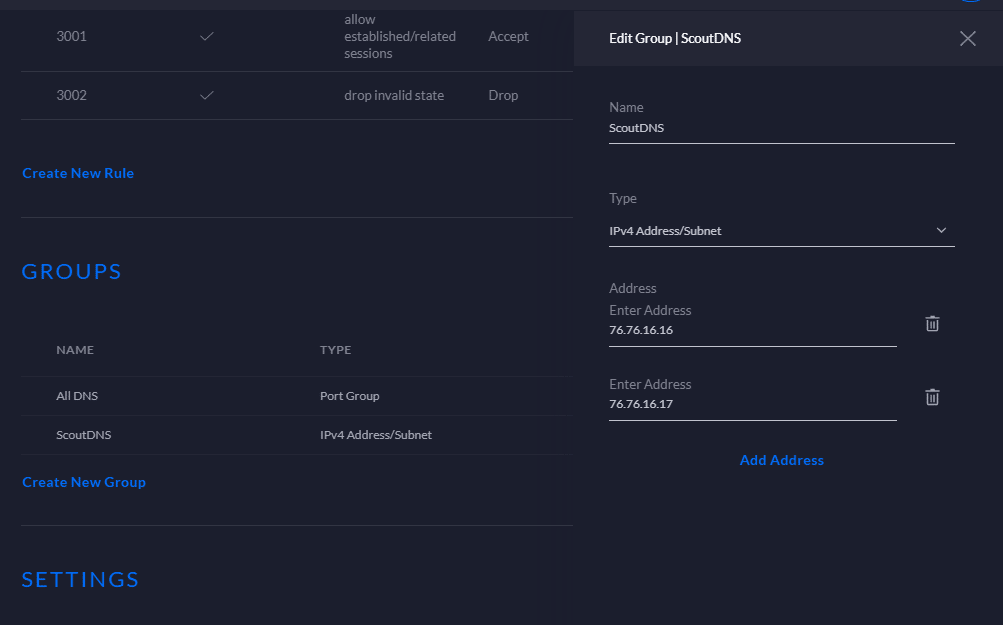
STEP 2) Configure IPv4 Address/Subnet Group (Resolver Group)
Next we will configure the IP based object for our actual resolver IPs. In this instance we use our default primary and secondary ScoutDNS IPs but you can configure any resolvers that you may want to allow on your network. On my network I call it ScoutDNS.
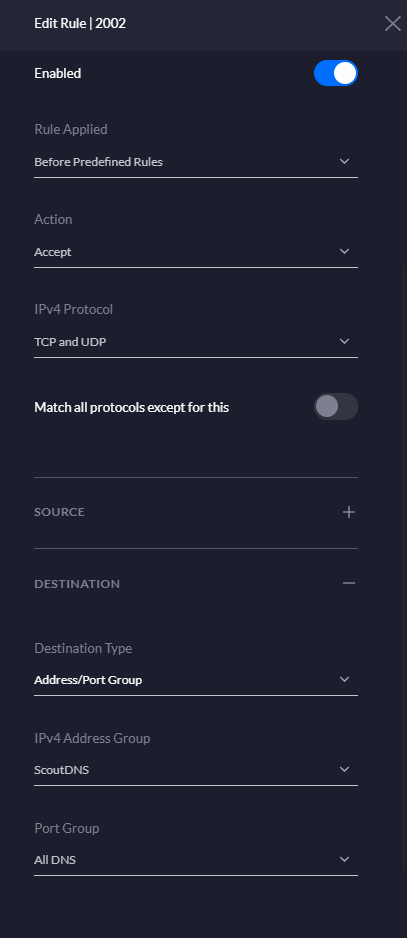
STEP 3) Create Firewall Rule allowing the Resolver Group
Now create a WAN Out firewall rule that allows ScoutDNS. Remember, although UDP is the default protocol for DNS, TCP can all be used. For this reason select both” TCP and UDP” under the IPv4 Protocol selection.
Here are the key settings:
Rule Type: WAN Out
Rule Applied: Before Predefined Rules
Action: Accept
IPV4 Protocol: TCP and UDP
Destination Type: Address/Port Group
IPv4 Address Group: Your Group Name
Port Group: All DNS
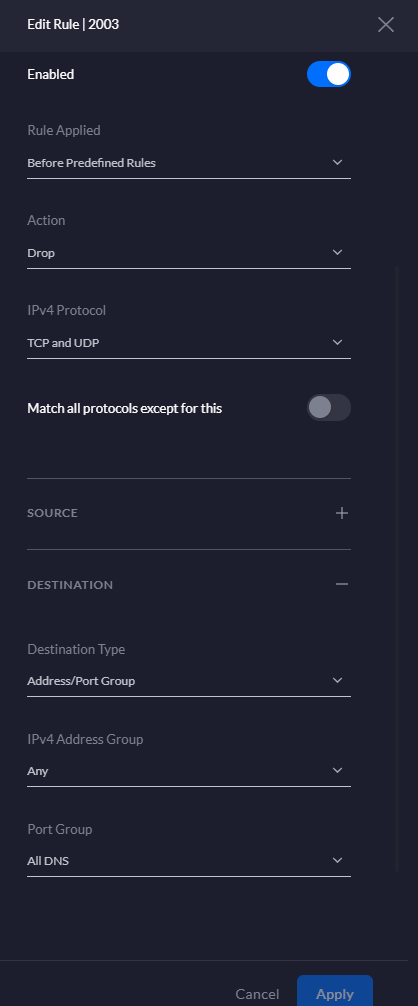
STEP 4) Create Firewall Rule Dropping all traffic on the DNS Port Group
Finally create a WAN Out Firewall Rule prohibiting all other DNS traffic on port 53. The Accept rule created in step 3 for our preferred resolvers will override.
Key Settings:
Type: WAN Out
Rule Applied: Before Predefined Rules
Action: Drop
IPv4 Protocol: TCP and UDP
Port Group: All DNS
Quick Tip:
You can add additional revolvers at any time by editing the Allowed Resolver group.
If using multiple services or a NAT type multi-policy, you can allow specific resolvers based on subnet/VLAN
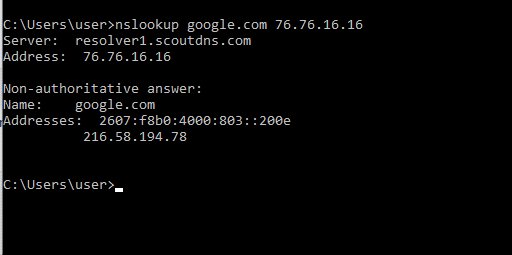
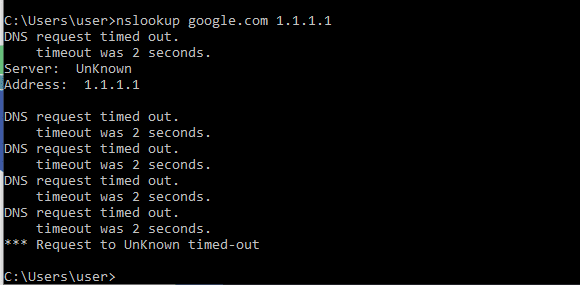
Test and Confirm
If you want to test your configuration simply run a couple of NSLOOKUP commands from a command prompt:
Want to Super Charge DNS Security and Visibility on your Unifi Network?
Check out our Cloud Managed on premise DNS Relay that runs on anything from a Linux PC to Raspberry Pi. Set policy by subnet and log all DNS queries to sites based on internal LAN IP.