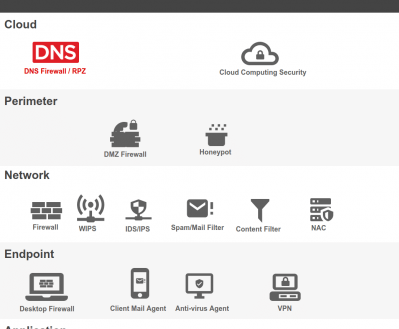
Proper cybersecurity begins with layers and monitoring the DNS layer will give you a better position for insuring a healthy and safe network. Here are 5 actions you can take to improve your security profile.
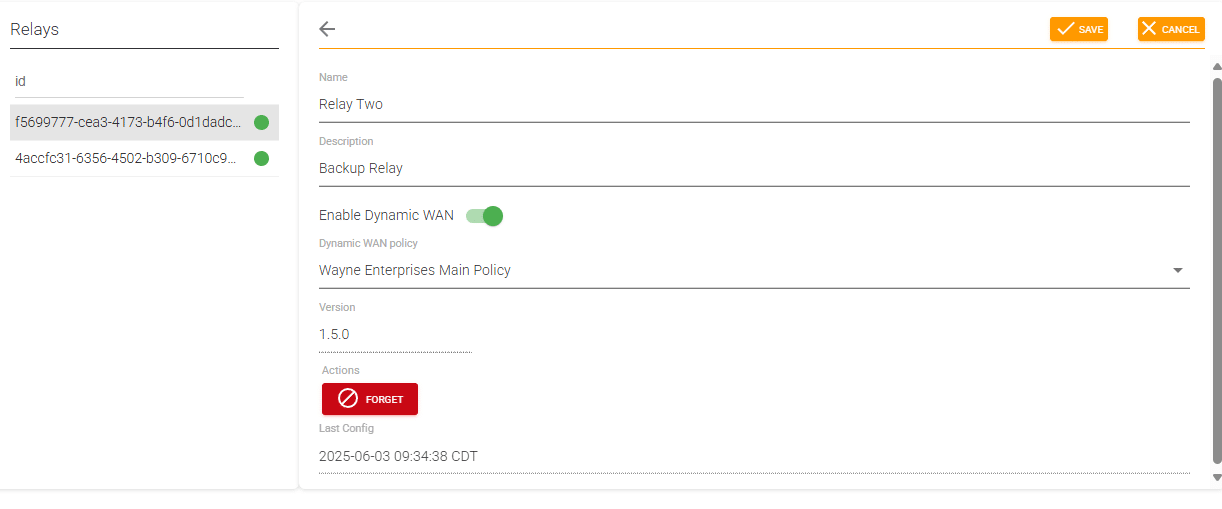
New Relay Features – Dynamic WAN and Fail Open
We have long supported dynamic DNS entries for WAN IP interfaces in network-based deployments at ScoutDNS. While this feature has been sufficient for most users